Resources / Featured Topics
Your First Line of Network Defense

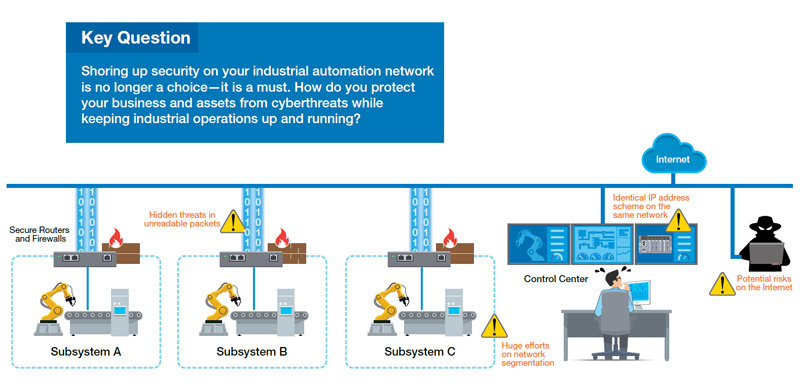
In the IIoT era, previously unconnected systems are now connected over private or public networks in order to gain more insights and improve productivity. The downside of greater connectivity is that industrial networks are no longer immune to cyberthreats. The upside is a growing chorus of experts is sharing their expertise to help you shore up cybersecurity in your industrial network. Generally speaking, two methods are available for implementing industrial cybersecurity. One method is to secure the foundation of your network infrastructure and only allow authorized traffic to flow to the designated areas. The other method involves identifying critical assets and applying layered protection. Industrial secure routers and firewalls are essential to both of these methods as they are deployed at the front lines to prevent unauthorized access and traffic to your industrial networks.
Key Criteria for Choosing Industrial Secure Routers and Firewalls
Industrial control systems can apply a defense-in-depth approach to protect critical equipment and secure various locations, device cells, function zones, and factory sites on your automation network. Defense-in-depth cybersecurity includes three types of controls: physical, technical, and administrative. First, implement physical controls by segmenting your network and creating boundaries between each segment. Next, apply technical controls by securing network traffic or filtering data packets. Lastly, enhance administrative security by managing IP addresses and adopting strong security policies. Secure routers and firewalls provide an excellent way to achieve defense-in-depth cybersecurity on your network, but how do you choose the right router or firewall for your industrial application? Consider the following criteria.
Adding Firewalls Without Changing Your Network
Network segmentation involves breaking down the network into physical or logical zones with industrial firewalls. A firewall is an access control device that looks at the IP packet, compares the packet with preconfigured policy rules, and decides whether to allow, deny, or take some other action on the packet. Generally speaking, firewalls can be either routed or transparent, and the type you will need depends on the requirements of your application. Unlike routed firewalls, transparent firewalls allow you to keep the same subnet so that you can easily add firewalls to an existing network.
With transparent firewalls, you also do not need to change the network topology. Transparent firewalls are suitable for protecting critical devices or equipment inside a control network where network traffic is exchanged within a single subnet. Furthermore, you do not need to reconfigure IP subnets because transparent firewalls do not participate in the routing process.
Detect Threats and Protect Critical Data
Firewalls are akin to gatekeepers. Unfortunately, determined intruders may still be able to get through the gates on a segmented network. That’s why you need to constantly check the traffic that passes through the gates you have established. One way to achieve this is to filter out unwanted commands such as write or configure commands that could cause industrial processes to fail when needed or unnecessarily trigger a safe state during production. Therefore, it is important for industrial secure routers and firewalls to support industrial protocol filtering at the command level (read, write, etc.) for more fine-grained whitelisting control. If you want to secure the transmission of confidential data, you may want to consider building secure tunnels for site-to-site communications. In some scenarios, communications over public or untrusted networks will definitely require secure encrypted data transmissions. Under such circumstances, you may also want to consider VPN capability when choosing your industrial secure routers and firewalls.

Getting Your Firewalls and Network Under Control
In industrial applications, hundreds or thousands of firewalls could be installed to control
data traffic and protect field equipment from malicious attacks. Furthermore, even more IP
addresses could be on your network. As networks continue to expand, managing all of the devices,
firewall rules, and IP addresses become more complicated. Therefore, network address translation
(NAT) provides a very important function when you deploy industrial secure routers and firewalls.
NAT allows you to reuse machine IP address schemes on the same network and connect multiple devices
to the Internet, using a smaller number of IP addresses. This not only significantly reduces
maintenance efforts and administrative overhead, but also provides simple network segmentation. In
addition, it enhances security for private networks by keeping internal addressing private from the
external network. Watch our video to learn more.
Finding the right secure router or firewall for your application brings you to the halfway mark in successfully beefing up your industrial network security. Using three criteria to help you make the right choice can remove some of the guesswork. For instance, a highly integrated industrial multiport secure router with firewall/NAT/VPN and managed Layer 2 switch functions, such as the Moxa EDR-810 Series, provide everything you need. Nevertheless, whatever solution you ultimately choose should fit your specific application requirements.

